Yes, SaaS can be secure for sensitive data. It depends on various factors.
Understanding these factors is crucial. Many businesses rely on Software as a Service (SaaS) for their operations. This raises questions about data security. Is it safe to store sensitive information on these platforms? SaaS providers often claim top-notch security, but how true is this?
In this blog post, we will explore the security measures SaaS providers use. We will also discuss potential risks and how to mitigate them. This will help you make an informed decision about using SaaS for your sensitive data.
Introduction To Saas Security
As businesses move to cloud-based solutions, the security of SaaS (Software as a Service) becomes crucial. The need to protect sensitive data is more important than ever. This section will explore how secure SaaS is for handling sensitive data.
What Is Saas?
SaaS stands for Software as a Service. It is a software distribution model.
With SaaS, applications are hosted by a third-party provider. They are made available to customers over the internet. Users can access these applications through a web browser.
SaaS offers many benefits:
- Easy access from any device.
- Lower upfront costs.
- Automatic updates.
Importance Of Data Security
Data security is crucial for any business. Especially those handling sensitive information.
There are several reasons why data security is important:
- Protects confidential information.
- Prevents unauthorized access.
- Ensures data integrity.
Without strong security measures, sensitive data is at risk. This can lead to data breaches, financial loss, and reputational damage.
In the SaaS model, the responsibility of data security is shared. Both the provider and the customer must implement robust security practices.
| Provider’s Responsibilities | Customer’s Responsibilities |
|---|---|
| Data encryption | Strong password policies |
| Regular security audits | User access management |
| Compliance with standards | Training employees |
Both parties must work together. This ensures the highest level of data security.
Credit: www.polymerhq.io
Common Security Threats
Software as a Service (SaaS) is a popular choice for many businesses. Yet, it is crucial to understand the common security threats that can impact the safety of sensitive data. Below we discuss some of the most significant threats to SaaS security.
Data Breaches
Data breaches are a major concern for any SaaS provider. Unauthorized access to sensitive data can result in financial loss, legal repercussions, and damage to reputation. Hackers use various methods to gain access to data, including:
- Phishing attacks
- Exploiting software vulnerabilities
- Man-in-the-middle attacks
Companies must implement strong encryption and access control measures to safeguard data. Regular security audits and employee training also help in reducing the risk of data breaches.
Malware And Ransomware
Malware and ransomware can significantly disrupt operations. They can lock users out of their systems or steal sensitive information. Malware is any software designed to harm or exploit devices, while ransomware demands payment to restore access to data.
Effective protection involves:
- Using antivirus and anti-malware software
- Regular software updates to patch vulnerabilities
- Implementing firewalls and intrusion detection systems
Backup strategies are crucial. Regular backups ensure data can be restored if an attack occurs.
Security Measures In Saas
Ensuring the security of sensitive data is crucial in SaaS (Software as a Service). SaaS providers implement various security measures to protect data. Let’s explore the key security measures adopted in SaaS.
Encryption Techniques
One of the primary security measures in SaaS is encryption. Encryption converts data into a coded form. Only authorized users can decode it. SaaS providers use both encryption at rest and encryption in transit.
Encryption at rest protects data stored in databases. Encryption in transit secures data as it travels between users and servers. Common encryption standards include AES-256 and SSL/TLS.
| Encryption Type | Description |
|---|---|
| Encryption at Rest | Protects data stored in databases. |
| Encryption in Transit | Secures data traveling between users and servers. |
Access Controls
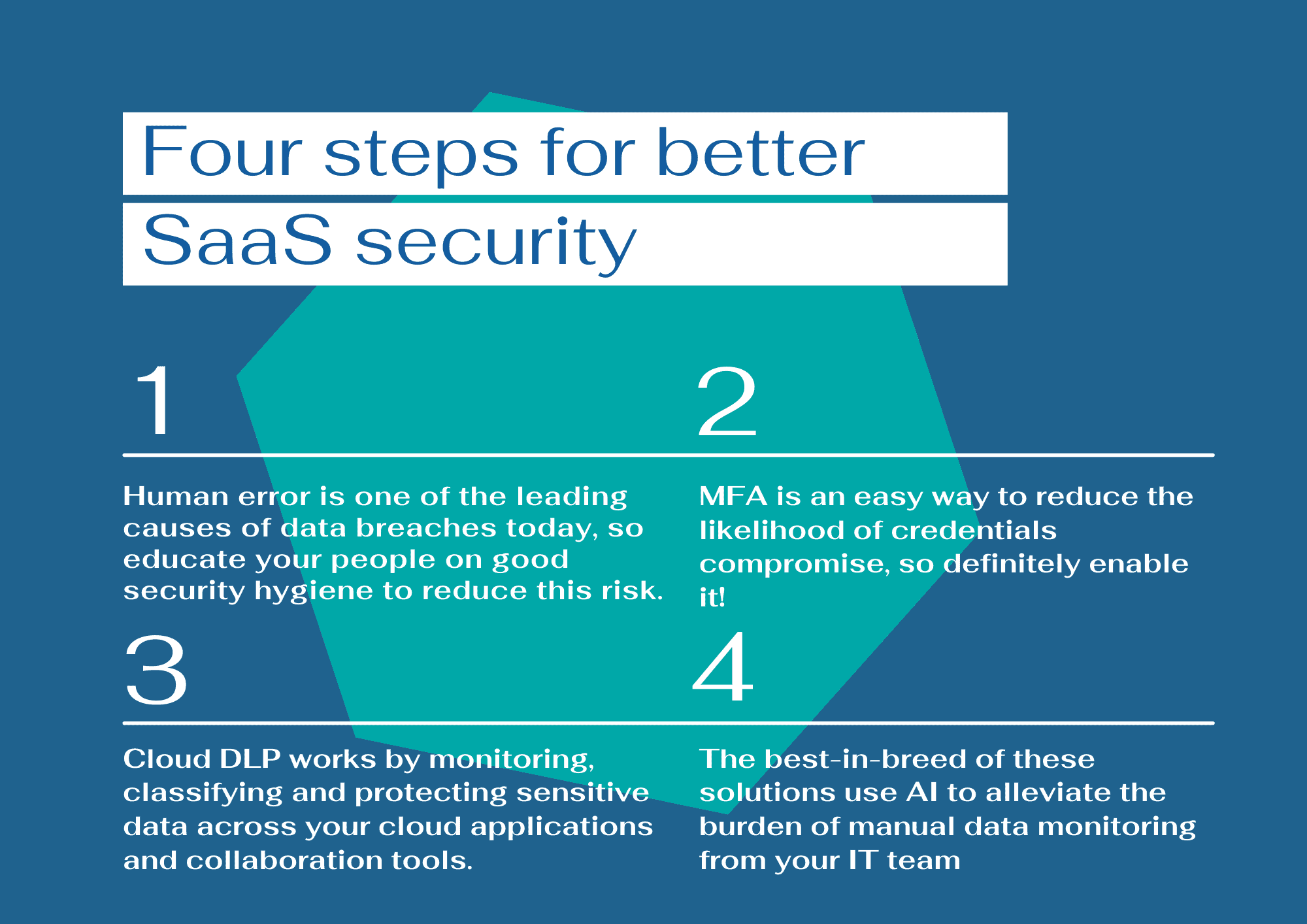
Access controls ensure that only authorized users can access sensitive data. SaaS providers use various access control methods. These include role-based access control (RBAC) and multi-factor authentication (MFA).
RBAC assigns access permissions based on user roles. For example, an admin might have more access than a regular user. MFA adds an extra layer of security. Users must verify their identity through multiple methods. This could be a password plus a code sent to a phone.
- Role-Based Access Control (RBAC)
- Multi-Factor Authentication (MFA)
Access controls help prevent unauthorized access. They ensure sensitive data remains secure.
Compliance And Regulations
When considering the security of SaaS for sensitive data, compliance and regulations play a crucial role. These standards ensure that sensitive data is protected and handled correctly. SaaS providers must adhere to various regulations to gain trust and ensure data security. Let’s explore some of the key regulations SaaS providers follow.
Gdpr
The General Data Protection Regulation (GDPR) is a regulation in the European Union. It governs data protection and privacy for individuals within the EU. SaaS providers that handle data of EU citizens must comply with GDPR.
- Data protection: SaaS providers must ensure data is protected against unauthorized access.
- Data breach notification: They must inform users about data breaches within 72 hours.
- User consent: Providers need explicit consent from users to process their data.
Hipaa
The Health Insurance Portability and Accountability Act (HIPAA) is a US regulation. It protects sensitive patient health information from being disclosed without consent. SaaS providers dealing with healthcare data must comply with HIPAA.
- Data encryption: Sensitive health data must be encrypted during transmission and storage.
- Access control: Only authorized personnel should access patient data.
- Audit controls: Providers must track and log access to patient data.
Compliance with these regulations is essential for SaaS providers. It ensures the security and integrity of sensitive data. These measures build trust with users and demonstrate a commitment to data protection.
Evaluating Saas Providers
Choosing a SaaS provider for your sensitive data requires careful evaluation. Ensuring the highest level of security involves looking into various aspects of the provider’s practices. Two essential areas to focus on are Security Certifications and Vendor Risk Assessment. These elements help in determining the reliability and security of the SaaS provider.
Security Certifications
Security certifications are crucial in evaluating SaaS providers. They act as proof that the provider follows industry standards for data protection. Common certifications include:
- ISO/IEC 27001: This standard specifies the requirements for an information security management system (ISMS).
- SOC 2: This certification focuses on five “trust service principles” – security, availability, processing integrity, confidentiality, and privacy.
- GDPR Compliance: For companies handling data of EU citizens, GDPR compliance is mandatory.
These certifications ensure that the provider has robust security measures in place. They cover aspects such as encryption, access control, and incident management.
Vendor Risk Assessment
Conducting a vendor risk assessment is another crucial step. This process involves evaluating the potential risks associated with using the SaaS provider. Key areas to assess include:
- Data Encryption: Ensure that data is encrypted both at rest and in transit.
- Access Controls: Verify that the provider has strict access controls in place.
- Incident Response: Check the provider’s incident response plan and their history of handling data breaches.
- Third-Party Audits: Confirm that the provider undergoes regular third-party security audits.
By evaluating these factors, you can better understand the provider’s security posture. This assessment helps in making an informed decision about the safety of your sensitive data.

Credit: www.strac.io
Best Practices For Saas Security
Ensuring the security of sensitive data in SaaS applications is crucial. Following best practices helps safeguard your information and build trust. Let’s explore key strategies to keep your data secure.
Regular Audits
Conduct regular audits to identify vulnerabilities. Regular checks help detect security gaps early. An audit involves reviewing access controls and monitoring activity logs. This process ensures compliance with security standards.
Schedule audits at least twice a year. Frequent audits help maintain a secure environment. Use automated tools for continuous monitoring. This proactive approach minimizes risks and enhances data protection.
Employee Training
Train employees on security protocols. Educated staff can better handle sensitive data. Conduct workshops and seminars on cybersecurity practices. Include topics like phishing, password management, and data encryption.
Regular training sessions keep security knowledge up-to-date. Ensure employees understand the importance of data security. Encourage them to report suspicious activities immediately. A well-informed team is your first line of defense.
Emerging Trends In Saas Security
As more businesses rely on SaaS solutions, ensuring the security of sensitive data is crucial. Emerging trends in SaaS security focus on advanced technologies and architecture to protect data. Key trends include AI and machine learning, and zero trust architecture.
Ai And Machine Learning
AI and machine learning play a pivotal role in SaaS security. These technologies can identify and respond to threats in real-time. They analyze vast amounts of data to detect unusual patterns. This helps in predicting and preventing potential attacks.
AI algorithms continuously learn from new data. This makes them more effective over time. Machine learning models can automate threat detection and response. This reduces the reliance on human intervention and speeds up the security process.
Benefits of AI and machine learning in SaaS security include:
- Real-time threat detection
- Automated response to security incidents
- Improved accuracy in identifying threats
- Reduced manual workload for security teams
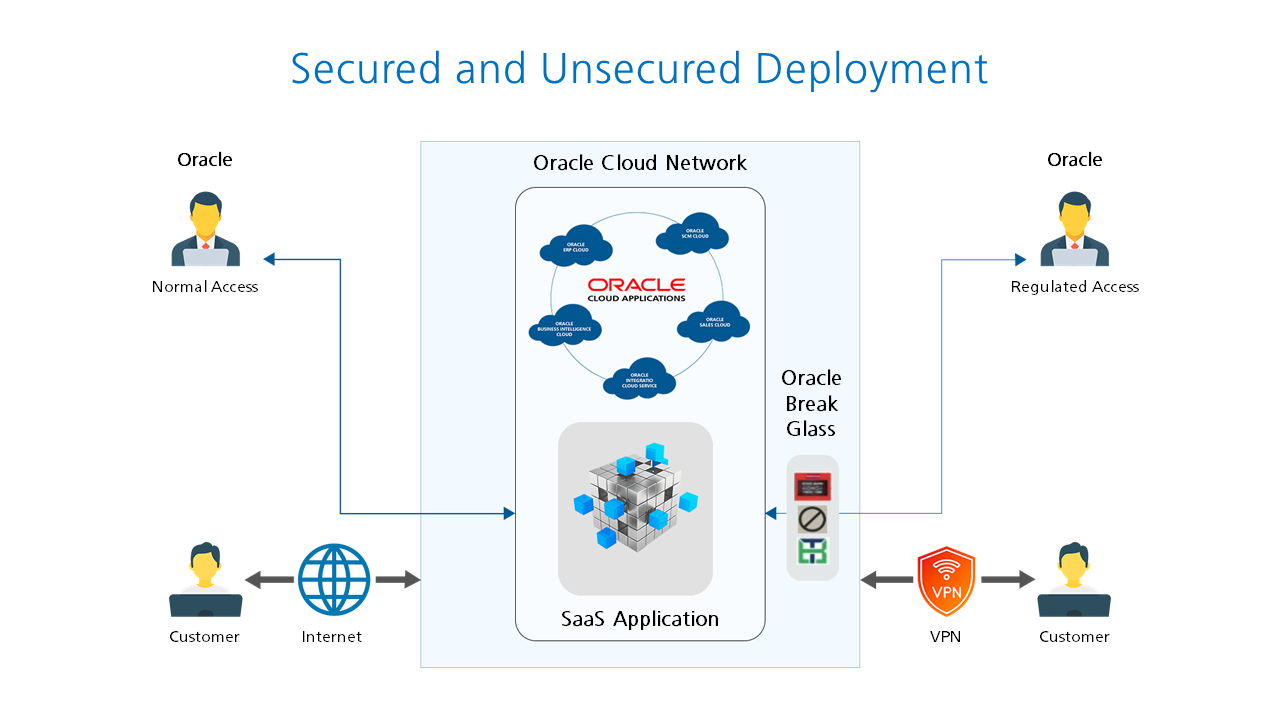
Zero Trust Architecture
Zero trust architecture is another emerging trend in SaaS security. This model operates on the principle of “never trust, always verify.” It assumes that threats can come from both inside and outside the network.
Zero trust requires strict identity verification for every user and device. It ensures that only authenticated and authorized users can access sensitive data. This reduces the risk of unauthorized access and data breaches.
Key components of zero trust architecture include:
- Multi-factor authentication (MFA)
- Least privilege access
- Continuous monitoring
- Micro-segmentation
By implementing zero trust architecture, businesses can enhance their security posture. It provides a robust framework for protecting sensitive data in SaaS environments.
Credit: www.ltimindtree.com
Frequently Asked Questions
Is Saas Secure For Storing Sensitive Data?
Yes, SaaS can be secure for sensitive data. Providers use encryption, regular audits, and compliance with security standards to protect data.
What Security Measures Do Saas Providers Use?
SaaS providers use encryption, multi-factor authentication, and regular security audits. They also comply with industry standards and regulations.
How Does Encryption Protect Sensitive Data In Saas?
Encryption converts data into a coded format. Only authorized users with decryption keys can access the original information, ensuring data security.
Are Saas Providers Compliant With Security Regulations?
Most reputable SaaS providers comply with security regulations like GDPR, HIPAA, and SOC 2. Compliance ensures they follow best practices for data protection.
Conclusion
SaaS offers robust security for sensitive data. Encryption protects data from breaches. Regular updates ensure the latest security patches. User authentication adds another layer of safety. Choose reputable providers with strong security records. Always read their security policies. Monitor and manage access to your data.
Stay informed about potential threats. SaaS can be safe when used correctly. Prioritize security to protect your sensitive information.