SaaS companies prioritize user data privacy to build trust. They use advanced techniques to protect sensitive information.
In a world where data breaches are common, ensuring user data privacy is crucial. SaaS companies handle vast amounts of data daily. Users trust these companies with their personal and business information. This trust hinges on the companies’ ability to protect data from unauthorized access.
Understanding how SaaS companies ensure user data privacy can help users feel secure. It also highlights the importance of data protection practices in the tech industry. Let’s explore the measures SaaS companies take to keep user data safe.
Importance Of Data Privacy
Data privacy is crucial for SaaS companies. It ensures user data is safe. Users trust companies that protect their information. Data breaches can damage this trust. Data privacy also helps companies comply with legal standards. Below are key reasons why data privacy is important.
User Trust
Users must trust that their data is safe. Protecting data builds this trust. Users feel more secure sharing personal information. Trust leads to customer loyalty. Loyal customers are more likely to recommend the service.
Legal Compliance
SaaS companies must follow data protection laws. Laws like GDPR and CCPA set strict rules. Non-compliance can result in heavy fines. Compliance ensures the company avoids legal trouble. It also shows users that the company values their privacy.
| Reason | Description |
|---|---|
| User Trust | Data privacy builds and maintains user trust. Trust is crucial for customer loyalty. |
| Legal Compliance | Following data protection laws avoids fines and legal issues. Compliance also boosts user confidence. |
In summary, data privacy is essential. It fosters user trust and ensures legal compliance. SaaS companies must prioritize protecting user data.

Credit: www.cookieyes.com
Data Encryption Techniques
Data encryption techniques are vital for SaaS companies to ensure user data privacy. By securing data through encryption, companies prevent unauthorized access. Let’s explore two primary encryption methods used: in-transit encryption and at-rest encryption.
In-transit Encryption
In-transit encryption protects data as it travels from one point to another. This means data is safe while moving between a user’s device and a SaaS company’s servers. The most common method is Transport Layer Security (TLS). TLS ensures data remains confidential and intact. Hackers find it hard to intercept or alter data with TLS. Another widely used method is Secure Sockets Layer (SSL). SSL creates a secure connection between the user and the server. It uses encryption keys to protect the data during transmission. Both methods are essential for maintaining data integrity and user trust.
At-rest Encryption
At-rest encryption secures data stored on servers or databases. It ensures data remains safe even if unauthorized access occurs. Advanced Encryption Standard (AES) is a popular choice for at-rest encryption. AES uses symmetric key encryption, which is efficient and secure. It encrypts data blocks, making them unreadable without the correct key. Another method is file-level encryption. This technique encrypts individual files or directories. It provides an added layer of security for sensitive information. Both AES and file-level encryption protect user data from breaches.
Access Control Measures
Access control measures are crucial for SaaS companies to ensure user data privacy. These measures help restrict unauthorized access and protect sensitive information. Here, we will discuss key strategies SaaS companies use to secure user data through effective access control.
Role-based Access
Role-based access control (RBAC) assigns permissions based on the user’s role within the organization. This ensures that each user has access only to the data necessary for their role. By limiting access, the risk of data breaches reduces significantly.
- Admin: Full access to all data and settings.
- Manager: Access to team data and management tools.
- Employee: Access to personal and team-specific data.
Using RBAC, SaaS companies can efficiently manage permissions and maintain data security.
Multi-factor Authentication
Multi-factor authentication (MFA) enhances security by requiring multiple forms of verification. This method combines something the user knows (password) with something the user has (security token) or something the user is (fingerprint).
- Enter username and password.
- Receive a code on a mobile device.
- Enter the code to gain access.
MFA adds an extra layer of protection, making it harder for attackers to gain access.

Credit: www.zluri.com
Regular Security Audits
Regular security audits are crucial for SaaS companies to ensure user data privacy. These audits help identify vulnerabilities and strengthen security measures. They involve both internal and third-party assessments to maintain high standards. Let’s explore these audit types in detail.
Internal Audits
Internal audits are conducted by the company’s own team. They review and analyze the security protocols in place. This team checks for any weak points in the system. They ensure all data protection measures meet the company’s standards. Regular internal audits help in maintaining consistent security practices.
Third-party Audits
Third-party audits provide an unbiased review of the company’s security. Independent experts conduct these audits to evaluate the system’s robustness. They identify potential threats that internal teams might overlook. These audits add an extra layer of assurance. They help in maintaining transparency and trust with users.
Data Anonymization Methods
Data anonymization methods play a crucial role in ensuring user data privacy for SaaS companies. These methods transform identifiable data into a form where individuals cannot be easily recognized. This process helps protect user privacy and complies with data protection regulations. Let’s explore two common data anonymization methods: tokenization and pseudonymization.
Tokenization
Tokenization replaces sensitive data with unique symbols or tokens. These tokens cannot be reverse-engineered to reveal the original data. For example, a credit card number might be replaced with a random string of characters. The original data is stored securely in a separate database. Only authorized systems can map tokens back to the original data. This method ensures sensitive information remains protected even if the tokens are exposed.
Pseudonymization
Pseudonymization involves replacing private data with pseudonyms or fictitious identifiers. Unlike tokens, pseudonyms can sometimes be traced back to the original data using additional information. This method reduces the risk of data breaches by separating identifiable information from personal data. It allows for data analysis and processing without compromising user privacy. By using pseudonymization, SaaS companies can maintain a high level of security while still utilizing valuable data.
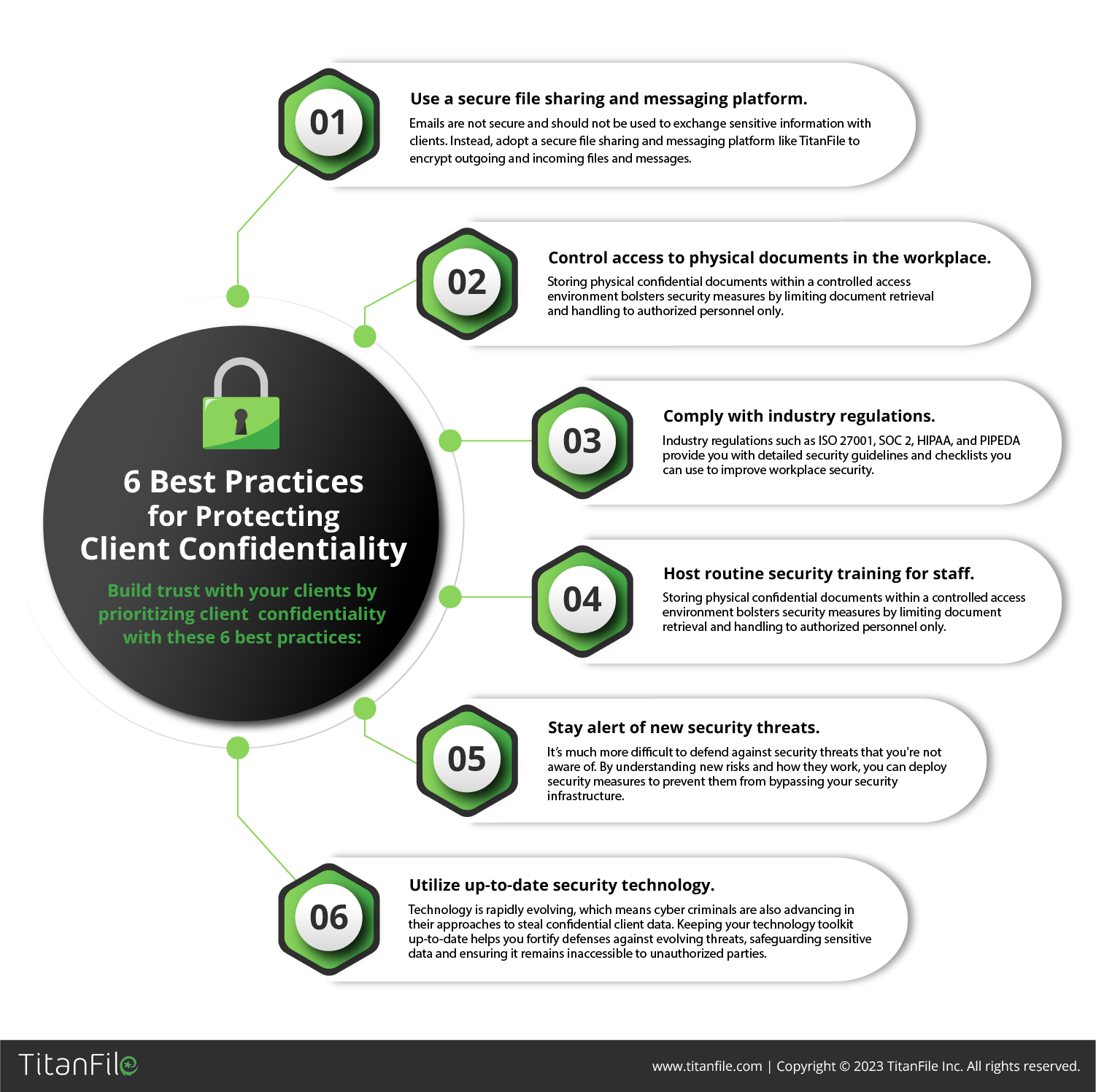
Credit: www.titanfile.com
User Consent Management
User consent management is crucial for SaaS companies. It ensures users know how their data is used. Companies need to get clear consent from users. This builds trust and ensures compliance with data privacy laws.
Good user consent management involves several key practices. These practices help protect user data. They also make sure users feel safe and informed. Let’s explore some important aspects.
Clear Privacy Policies
SaaS companies need clear privacy policies. These policies explain how user data is collected, used, and shared. They should be easy to read and understand. Users must know their rights and how their data is protected.
A well-written privacy policy builds trust. It shows that the company values user privacy. It also makes compliance with legal requirements easier.
Opt-in/opt-out Options
Users should have control over their data. SaaS companies must offer opt-in and opt-out options. This means users can choose to share their data or not. They can also change their preferences at any time.
Offering these options shows respect for user choices. It also helps ensure transparency and trust. Users feel more secure when they have control over their data.
Incident Response Plans
Incident Response Plans are vital for SaaS companies to protect user data. These plans help identify, manage, and resolve security incidents quickly. Effective incident response minimizes damage and ensures data privacy.
Breach Detection
Breach Detection is the first step in an incident response plan. SaaS companies use various methods to detect breaches. These methods include:
- Intrusion Detection Systems (IDS)
- Security Information and Event Management (SIEM) tools
- Regular security audits
These systems monitor for suspicious activities. They alert the team when they find a potential breach. Early detection is crucial to prevent data loss.
Breach Mitigation
Breach Mitigation involves actions taken to limit the impact of a breach. Once a breach is detected, the response team takes immediate steps to contain it. Common mitigation strategies include:
- Isolating affected systems
- Disabling compromised accounts
- Applying patches and updates
Quick action reduces the risk of further data exposure. The team also investigates the breach to understand its root cause. This helps in preventing future incidents.
Expert Opinions
Ensuring user data privacy in SaaS companies is a top priority. Experts in the field shed light on effective strategies and emerging trends. Their insights help companies stay ahead in protecting user data.
Industry Best Practices
Experts recommend using strong encryption methods. Encrypting data both in transit and at rest ensures added security. Regular security audits identify vulnerabilities and fix them promptly. Multi-factor authentication (MFA) adds an extra layer of protection. It requires users to provide multiple forms of identification. Data anonymization techniques help in protecting user identities. By masking personal information, companies reduce the risk of data breaches. Compliance with regulations like GDPR and CCPA is essential. These regulations set standards for data protection and user privacy.
Future Trends
Experts predict a rise in AI-driven security measures. AI can detect and respond to threats faster than humans. Blockchain technology may become more prevalent in data protection. It offers a transparent and tamper-proof way to manage data. Zero Trust Architecture is gaining popularity. It assumes that threats can come from inside or outside the network. This approach requires verification for every access request. Edge computing is another trend to watch. It processes data closer to its source, reducing exposure to breaches. Privacy by design will become a standard practice. It integrates data protection into the development process from the start.
Frequently Asked Questions
How Do Saas Companies Protect User Data?
SaaS companies use encryption, secure data centers, and regular security audits to protect user data. They also implement strict access controls and comply with data protection regulations.
What Encryption Methods Do Saas Providers Use?
SaaS providers typically use AES-256 encryption for data at rest and TLS for data in transit. These methods ensure that user data remains secure and inaccessible to unauthorized parties.
How Do Saas Companies Handle Data Breaches?
In the event of a data breach, SaaS companies follow an incident response plan. They notify affected users, investigate the breach, and take measures to prevent future incidents.
Are Saas Companies Compliant With Data Privacy Laws?
Yes, SaaS companies comply with data privacy laws such as GDPR, CCPA, and HIPAA. Compliance ensures that user data is handled responsibly and securely.
Conclusion
SaaS companies take user data privacy seriously. They implement strong security measures. Regular audits and updates keep data safe. Encryption protects sensitive information. User access controls restrict unauthorized entry. Compliance with regulations ensures legal protection. Clear privacy policies build user trust.
Continuous monitoring detects and responds to threats quickly. By prioritizing these practices, SaaS companies safeguard user data effectively. This commitment to privacy fosters confidence among users.